Penetration Testing Services
OVERVIEW

TYPES OF PENETRATION TEST
Our Penetration tests follow a structured process designed to uncover vulnerabilities before attackers do. Each phase plays a critical role in ensuring a thorough and ethical assessment of your systems.
Active Directory
We assess the security of your organisation’s Active Directory environment. It targets misconfigurations, privilege escalation paths, and authentication weaknesses. The scope includes enumeration of users, groups, trusts, and policies, exploitation of access controls, and testing lateral movement to identify risks that could compromise domain integrity.
Advisory Simulation
We mimic threat actor tactics to evaluate you organisation’s security posture under realistic conditions. The scope includes strategic attack planning, stealthy execution, and collaborative analysis. It focuses on identifying systemic weaknesses, testing incident response, and providing actionable insights aligned with threat intelligence and business risk.
Baseline
We provide a foundational assessment of your organisation’s security posture. It identifies common vulnerabilities across networks, systems, and applications using standard attack techniques. The scope includes scanning, exploitation, and reporting, offering a benchmark for future security improvements and helping prioritise remediation efforts based on risk exposure.
External Network
We assess the security of your publicly accessible systems and services. The scope includes identifying vulnerabilities in firewalls, web servers, VPNs, and other perimeter devices. It simulates attacks from outside the organisation to uncover exposure points, misconfigurations, and weaknesses that could be exploited by external threats.
Internal Network
We simulate an attacker who has been able to access your internal environment. The scope includes identifying vulnerabilities in workstations, servers, network devices, and access controls. It tests lateral movement, privilege escalation, and data access to uncover risks that could be exploited by malicious insiders or compromised accounts.
IoT (Internet of Things)
We evaluate the security of Internet of Things devices and their ecosystems. The scope includes assessing firmware, communication protocols, APIs, and mobile interfaces. It identifies vulnerabilities like weak authentication, insecure data transmission, and device misconfigurations, ensuring robust protection against exploitation and unauthorised access across connected environments.
Mobile App
Our Mobile App Penetration Test evaluates the security of your mobile applications across iOS and Android platforms. The scope includes testing for data leakage, insecure storage, weak authentication, and API vulnerabilities. It involves static and dynamic analysis to uncover flaws in code, communication channels, and user input handling.
Network Security
We evaluate the resilience of your organisation’s infrastructure against external and internal threats. The scope includes identifying vulnerabilities in firewalls, routers, switches, and endpoints. It involves scanning, exploitation, and analysis of network protocols, configurations, and access controls to uncover weaknesses and recommend security enhancements.
Phishing
We evaluate your organisation’s susceptibility to social engineering attacks. It involves crafting realistic phishing emails or messages to test employee awareness, response behaviour, and incident reporting. The scope includes scenario design, delivery, monitoring, and analysis to identify training gaps and improve security awareness across the workforce.
Red Team
We simulate real-world cyberattacks to assess your organisation’s security posture. We target systems, networks, and personnel using stealthy tactics to identify vulnerabilities, test detection and response capabilities, and improve overall resilience against advanced threats. The scope includes reconnaissance, exploitation, and post-exploitation activities.
Secure Code
We focus on identifying vulnerabilities within your Application Source Code. It involves manual and automated analysis to detect flaws like injection risks, insecure authentication, and poor error handling. The scope includes reviewing code structure, logic, and security controls to ensure robust, secure development practices are followed.
Web Application
Our Web Application Penetration Test identifies security flaws in your web-based systems. The scope includes testing for vulnerabilities like SQL injection, cross-site scripting (XSS), authentication bypass, and insecure APIs. It involves manual and automated techniques to assess input validation, session management, and access controls, ensuring robust protection against online threats.
Wireless
We will assess the security of your organisation’s wireless infrastructure. The scope includes identifying vulnerabilities in Wi-Fi configurations, encryption protocols, access controls, and rogue devices. It simulates attacks like unauthorised access, man-in-the-middle, and signal interception to uncover risks and strengthen wireless network defences.
PHASES OF PENTRATION TESTING
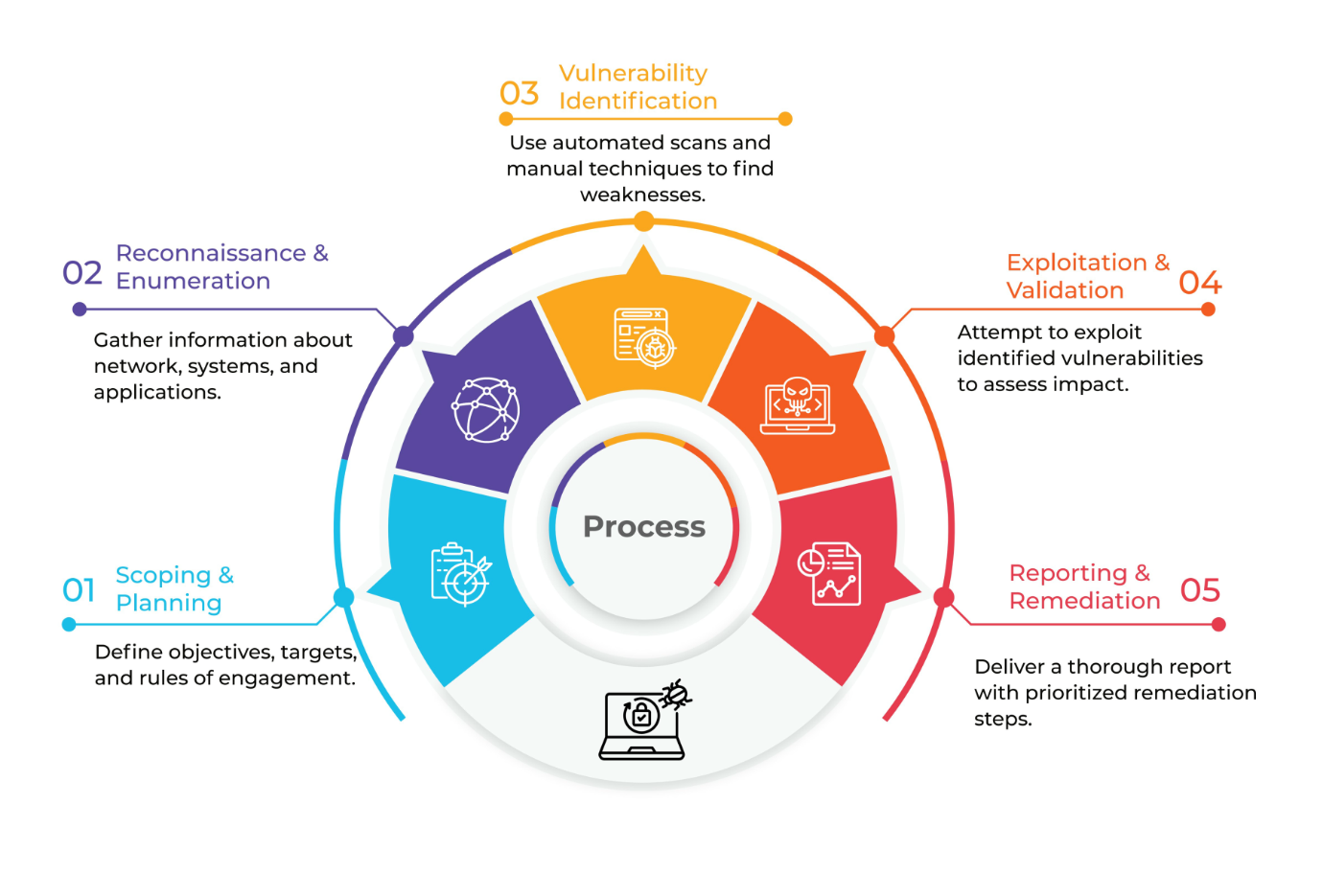
OUR PENETRATION TESTING METHODOLOGIES
1. Scope Identification
2. Threat Modelling
3. Testing Approaches
- Black Box Testing - We simulate an external attacker with no prior knowledge of your environment.
- White Box Testing - We are provided with full access to systems and code, mimicking an insider threat to your systems.
- Grey Box Testing - We are provided with partial access, representing a semi-informed attacker with limited internal knowledge.
4. Techniques Used
- Active Techniques - Involves direct engagement, such as exploitation attempts, payload injection, and privilege escalation.
- Passive Techniques - Includes network sniffing, open-source intelligence (OSINT), and reconnaissance without system interaction
- Social Engineering - Targets human vulnerabilities through phishing, impersonation, or phone-based manipulation.
5. Toolsets and Frameworks
6. Vulnerability Detection and Exploitation
7. Reporting and Remediation
8. Validation and Retesting
9. Compliance Alignment
10. Continuous Improvement

HOW MUCH ACCESS IS GIVEN TO THE PENETRATION TEAM
Required access will depend on the test type and objectives of the Penetration Test. In Black-box testing, minimal access is provided, simulating an external attacker. Grey-box testing offers limited internal knowledge, while White-box testing grants full access to systems, credentials, and architecture. Access is carefully controlled to balance realism with safety, ensuring accurate results without disrupting operations. Clear rules of engagement, scope boundaries, and escalation procedures are defined beforehand to guide the testers and protect critical assets. Ultimately, access is tailored to meet the organisation’s risk appetite and compliance requirements.
PENETRATION TESTING TECHNIQUES
Penetration testing techniques are categorised into Active and Indirect methods.
Active techniques involve direct interaction with systems, such as exploiting vulnerabilities, scanning ports, and attempting privilege escalation.
Indirect techniques focus on passive information gathering, like monitoring network traffic, analysing metadata, and conducting reconnaissance without triggering alerts. Together, they provide a comprehensive view of security weaknesses and potential attack paths.

HOW TO ENGAGE WITH US
Reach out to us either by:
- Hit the ‘Book a Meeting with us’ Button and find a convenient time to drop a meeting in the calendar
- Drop us an email to ‘contactus@northwickcyber.com’, we will get straight back to you
- Hit the ‘Contact Us’ button and let us know what you are interested in and we will contact you back
- Call us on ‘+61 1800 959 925’
Once we have communicated and understood your requirements we will organise a convenient Introduction and Consultation with the Cyber Team. Our process after that is :
1. Introduction and Initial Consultation
2. Scope Definition
3. Proposal and Agreement
4. Pre-Test Planning
5. Execution of Testing
6. Reporting and Remediation Guidance
7. Post-Test Validation
8. Strategic Integration
9. Project Closure
WHY CHOOSE US
Northwick Cyber delivers expert-led penetration testing tailored to your business needs. Our team combines industry-standard methodologies with advanced tools and custom techniques to uncover real-world vulnerabilities across networks, applications, and infrastructure. We provide clear, actionable remediation guidance and support, ensuring your organisation meets compliance requirements and strengthens its security posture. With a focus on transparency, collaboration, and continuous improvement, Northwick Cyber helps you stay resilient against evolving cyber threats.
We Provide Tailored Testing
Real-World Threat Simulation
Compliance Alignment
Clear Reporting
Expert Guidance
Continuous Improvement
Audit Readiness
Secure Operations
End-to-End Coverage
Post-Test Validation
Our Certifications